What is Secondary DNS?
A Secondary DNS is a DNS server that receives zone data from other servers, called Primary DNS, via a mechanism called AXFR. A secondary DNS server does not modify or alter zone data, but simply serves whatever zones and records you’ve set on the primary.
Sometimes secondary DNS is called “backup DNS” or “slave DNS”, meaning that secondaries just receive zones and makes them available to resolvers: it’s important to note that there’s no such thing from the point of view of DNS resolvers, which do not and cannot know the distinction between primary and secondary authoritative DNS of a given zone while choosing which one to ask records to.
Also, often people speak of primary and secondary DNS when referring to resolvers: I believe that this terminology is also slightly wrong, since both can be used and there’s no specific hierarchy for one being used rather then the other.
Now that I’m done telling half of the Internet that they’re wrong, it’s time to let you know that PTRDNS supports primary and secondary DNS zones in the same account, the only limitation is the number of zones in your plan. In this article we’ll see how you can configure a secondary zone at PTRDNS, while keeping a primary DNS at another provider (or in your own network if you self-host).
Secondary DNS should be on a different network
RFC 1034 recommends that each domain should have at least 2 authoritative servers, placed on different networks for protection against network failures at a single datacenter. By following this recommendation you can have several authoritative servers sharing the load, and secondaries can stay up and serve the copy of the zones they have even if the primary is down.
A popular variation of configuration is called “hidden primary”: you’re not forced to declare your primary DNS server anywhere, and by putting only the secondary servers in the SOA and NS records you can keep your primary hidden, while the secondaries will handle all of the traffic. Self-hosting enthusiasts can host their own primary DNS server in their own home network, transfer the zone data to PTRDNS and stop worrying about redundancy or DDoS.
How to configure a secondary DNS zone in PTRDNS?
Log on to your account at https://app.ptrdns.net and in the Dashboard click New TSIG Key, then choose a key name and algorithm:
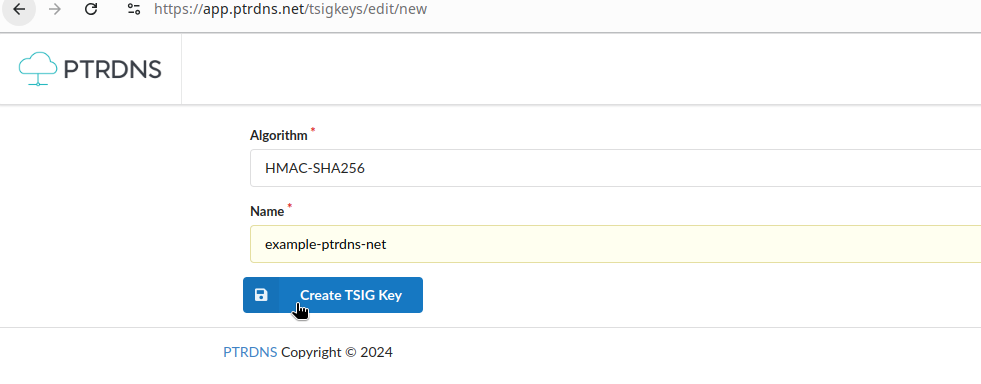
Once the key is created, copy its hash to the clipboard and save it somewhere, you will need to import it at your primary server.
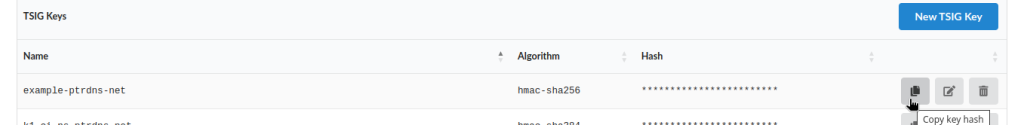
Choose a primary DNS server, with a static IPv4 or IPv6 address, and decide which zone you want to transfer: let’s use example.com for this exercise. PTRDNS strongly recommends using TSIG keys to authenticate zone transfers between primaries and secondaries, and to minimize the reliance on IP addresses as form of authentication.
If you’re using PowerDNS for your primary, you can use the following commands to generate a TSIG key and associate it to the zone:
$ pdnsutil import-tsig-key example-ptrdns-net \
hmac-sha256 \
YaD+vIR5..............................
$ pdnsutil activate-tsig-key example.com \
example-ptrdns-net primary
$ pdnsutil set-meta example.com \
ALLOW-AXFR-FROM 0.0.0.0/0
The last line allows any IPv4 address to transfer your zone, but only if the remote address produces the TSIG key example_ptrdns_net. If you prefer to restrict the IP address authorized to transfer your zone, you may put (ipv4 and ipv6 of intake.ns.ptrdns.net), which are the IP addresses corresponding to intake.ns.ptrdns.net.
Here’s a minimal set of record that will work for our purposes:
example.com 3600 IN NS ns1.example.com.
example.com 3600 IN NS tempo.ns.ptrdns.net.
example.com 3600 IN SOA ns1.example.com
hostmaster.example.com 0 10800 3600 604800 3600Go back to the PTRDNS Dashboard, click on New Zone and create a secondary zone, specifying the IP address of your primary server and the TSIG key:
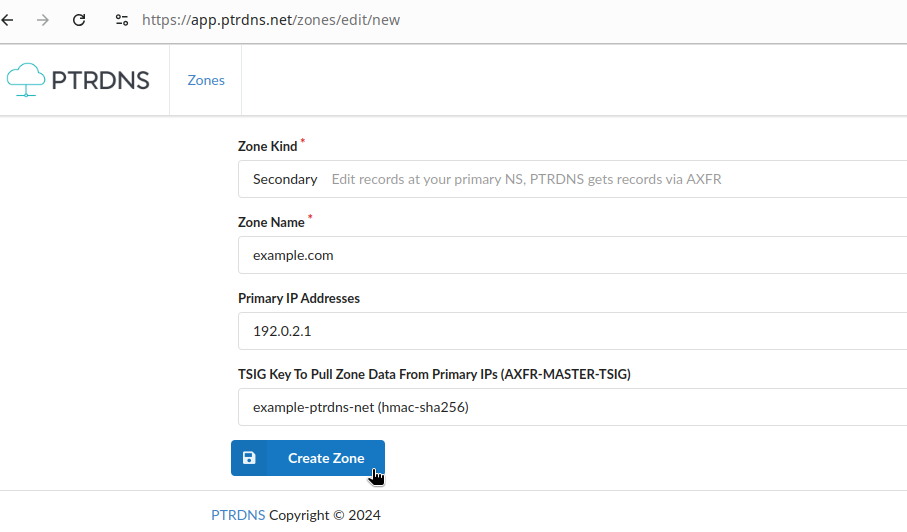
Save the changes and wait a few seconds for PTRDNS to pull the zone data from your primary, when this will be done you’ll be able to see the zone data in the PTRDNS editor (but not to change them, since for PTRDNS this is a read-only copy).
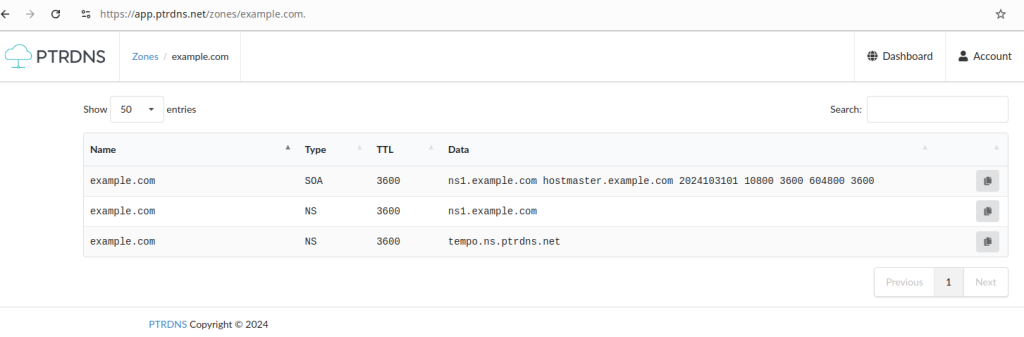
Don’t forget to add NS records pointing to at least one of PTRDNS nameservers, and to enter the same nameservers at your registrar: this way, resolvers will know that both your primary and PTRDNS nameservers have an authoritative copy of the zone data.
Last thing: set up NOTIFY, so your primary can notify PTRDNS whenever there are changes in your zone and PTRDNS can pull them in a matter of seconds. If you don’t do that, PTRDNS will still get the zone data but only every X minutes, the value of the REFRESH field in the zone’s SOA record.
I hope you enjoyed this short article and that you’ve seen how easy it is to add secondary zones to your current setup. You can sign up for PTRDNS and enjoy all of these features, plus large query quotas, short TTLs and PowerDNS API support from 5 EUR per month.
