What is Primary DNS?
A Primary DNS is a DNS server which acts as the source of the data for a DNS zone: it allows you to create a zone and modify its records, and make the zone available to resolvers on the Internet.
A primary DNS is often complemented by one or more Secondary DNS, which also are authoritative servers that resolvers can contact, but where the zone data is read-only and received from the primary.
You can combine primary and secondary DNS servers to achieve a more redundant setup and keep your website online if your primary is down.
A popular use case is called hidden primary: you have a primary DNS server and several secondaries, but only the secondary servers are listed at your registrar. With this setup, all Internet traffic goes to the secondaries and your primary DNS server doesn’t need to be up all the time, just enough for you to update records and to transfer the zone data to the secondaries.
In this article we’ll see how you can configure a primary zone at PTRDNS and add secondary servers on another provider.
Create a TSIG key
The first step is creating a TSIG key to secure the zone transfer. Securing a zone transfer with a TSIG key is not mandatory, but PTRDNS strongly recommends it to avoid rogue DNS servers getting copies of your DNS zones: without a TSIG key, the only alternative to reject unauthorized AXFR is set up an IP allowlist, which can be error-prone, more fragile if the IP addresses change and potentially vulnerable to IP spoofing.
Log on to your account at https://app.ptrdns.net and in the Dashboard click “New TSIG Key”, then choose an algorithm and a name for the key. You may use any name you want for the key, but we suggest a naming convention source-dest-zone which will make it easier to distinguish the keys once you have several. Let’s suppose that we’re operating on the example.com zone between PTRDNS and he.net, we can name our key ptrdns.net_he.net_example.com.

Once the key is created, you can move to the zone creation form.
Create a primary zone and associate the TSIG key
In the Dashboard, click on “New Zone”, then create a primary zone. Select our TSIG key in the TSIG-ALLOW-AXFR field, and do not forget to specify the IP addresses authorized to transfer the zone. By setting a TSIG key and putting 0.0.0.0/0 and ::0/0 as IP addresses, you allow AXFR from any IP address which will present the specified key, so make sure that this is exactly what you want.
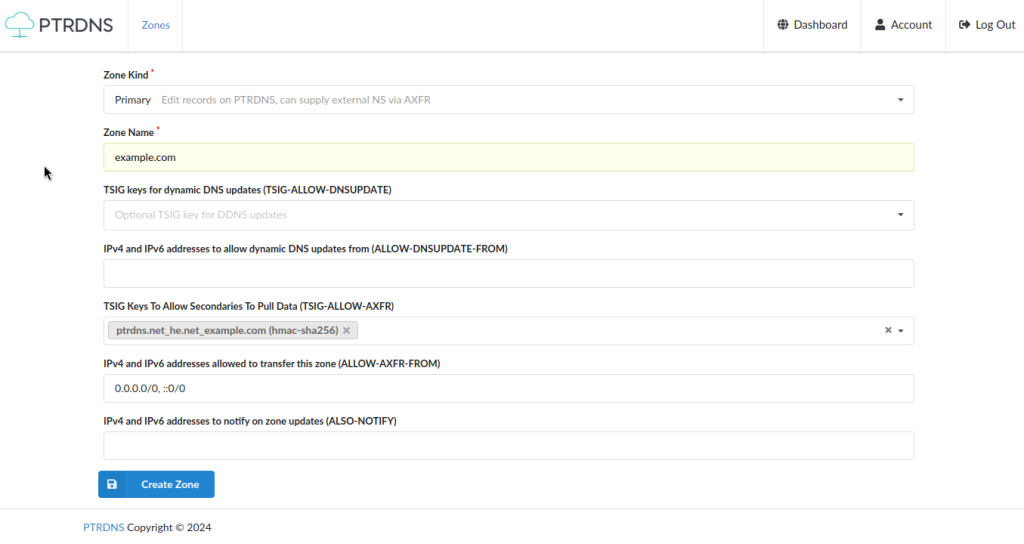
Note: PTRDNS supports native zones, which are zones that you can edit via the PTRDNS interface and API and that are served by PTRDNS nameservers only.
Add records to the primary zone
Now that the zone is created, you can add any record to it. Since we want to transfer this zone to he.net, and have it served by he.net nameservers, we need to add them to at least one of their NS record:
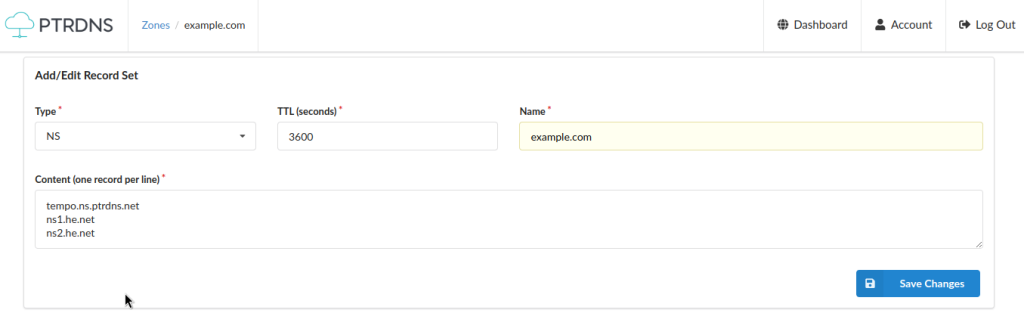
Note that we’re editing a record set, and thus we need to put all of the NS values in the Content field.
We can now add all the other records we need, such as A records for our website and MX records to receive mail. The final result looks like this:
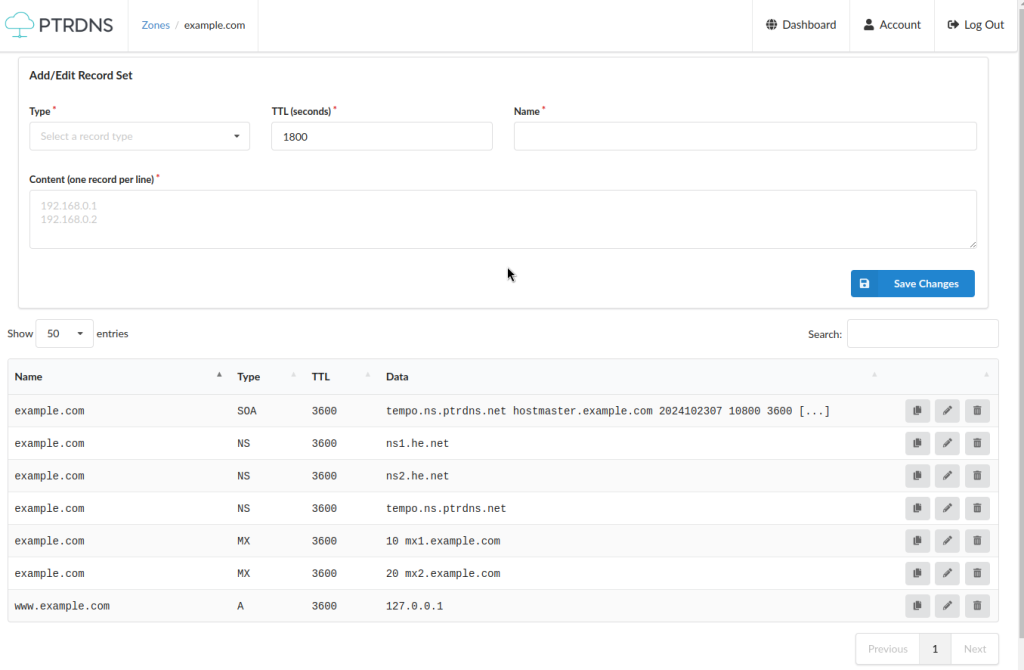
Our zone is now complete, let’s move to he.net and add a secondary zone there.
Create a secondary zone at another provider
Log on to the he.net interface, then click on “Add a new slave”. Fill in the form with the primary NS, in our case tempo.ns.ptrdns.net, and then the TSIG key details which you can copy from PTRDNS. Make sure to copy the exact hash algorithm, key name and hash value, otherwise the transfer will not work.
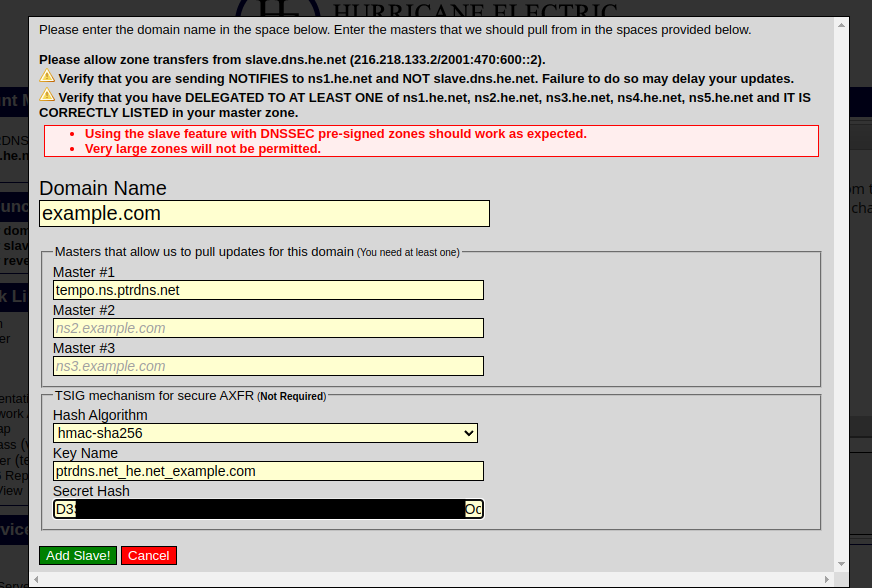
Wait a while, and then confirm that your zone appears in the he.net interface. Important: make sure to go to your registrar and delegate the zone nameserver to the exact values of the NS records set in the PTRDNS interface, otherwise no resolver will be able to see your changes.
Bonus: enable DNSSEC
If you enable DNSSEC on a primary zone at PTRDNS, the zone will propagate to the secondary servers with its DS records, even if the secondary DNS services you use don’t support DNSSEC explicitly.
Enabling DNSSEC at PTRDNS couldn’t be easier: in the Dashboard, click on the padlock icon, then click on Enable DNSSEC
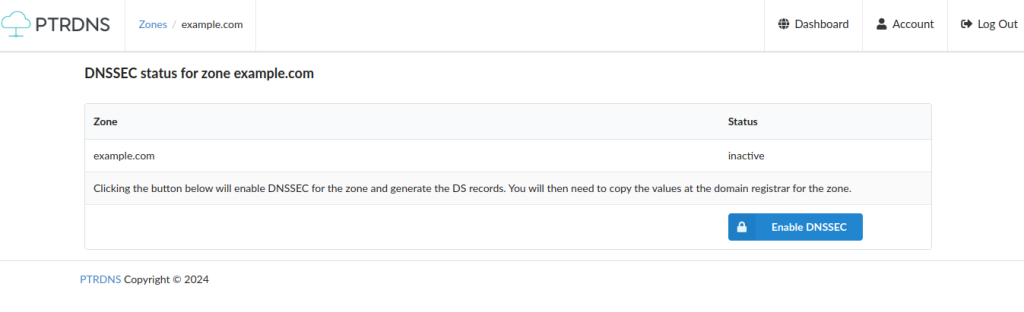
PTRDNS will sign the zone and then show you the DS records: copy the DS record values to your registrar, the secondary DNS will get the signatures via AXFR and your zone will be secured on all nameservers.
I hope you enjoyed this short article and that you’ve seen how easy it is to build a resilient DNS setup for your zones. You can sign up for PTRDNS and enjoy all of these features, plus large query quotas, short TTLs and PowerDNS API support from 5 EUR per month.
